On May 12, 2021 President Biden signed the Executive Order on Improving the Nation’s Cybersecurity into law. The fifteen-page document requires sweeping updates and overhauls of various cybersecurity processes and procedures, complete with deadlines for compliance..
Overview
In spite of being only fifteen pages in length, the executive order is detailed and complex. It’s quite easy to become overwhelmed by the dependencies between requirements and deadlines for completion. In this document, we have attempted to reduce this complexity by highlighting certain key aspects of the executive order and suggesting actions that can be taken now to help prepare your organization. In the cases not requiring immediate action, it’s still helpful to be aware of looming deadlines and intermediate publications that would be worth reviewing, which we have noted. It is our hope that this document provides some helpful clarity as you begin to plan for your organization’s adaptation.
As you will see, we have categorized the recommended responses to the requirements of the executive order as either WATCH or ACT. Items labeled WATCH are those that include intermediary steps before finalization, so immediate action is not recommended. Those labeled ACT are complete in the released order, so immediate response activities are recommended.
WATCH – Changes to the Federal Acquisition Regulation (FAR)
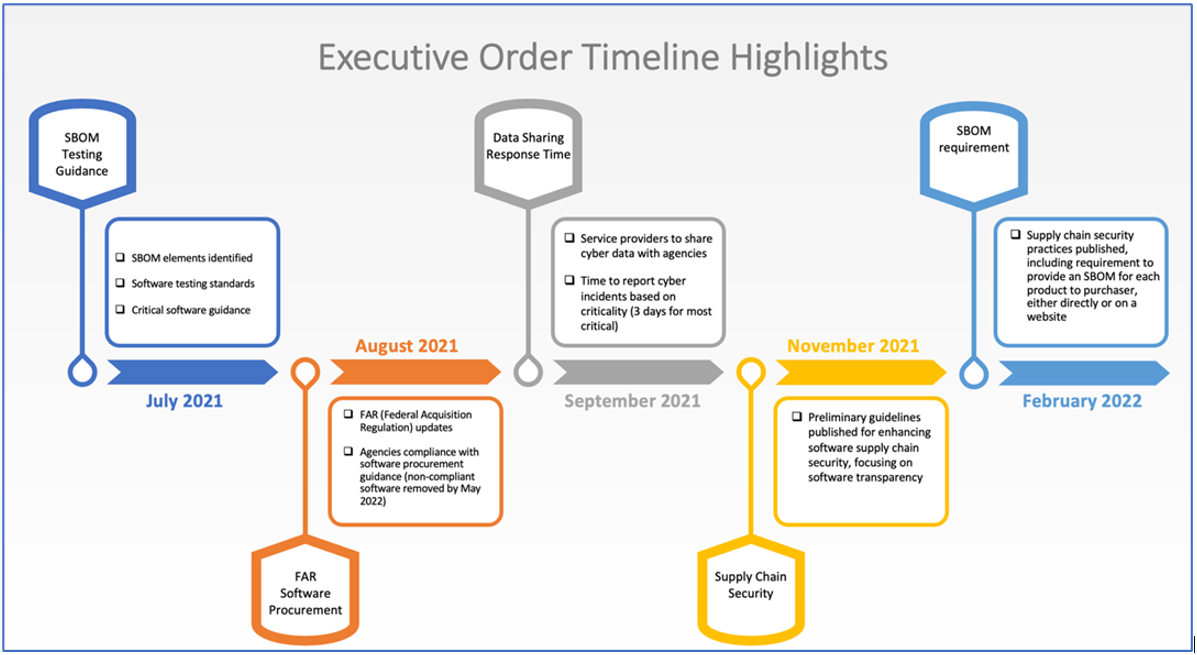
The regulations guiding the manner in which business is conducted with federal agencies will be modified. The extent of the modifications is dependent on a preliminary study of current regulations, which will be delivered by July 12, 2021. This study will analyze the Federal Acquisition Regulation (FAR) and the Defense Federal Acquisition Regulation Supplement (DFARS) contract language and requirements. Upon completion of this review, updates and changes to the regulations will be recommended.
Just ninety (90) days later, by October 12, 2021, these proposed updates will be published for public comment. Depending on the duration of the public comment period, the regulations could be updated before the end of this year. After publication, there will be an opportunity to provide feedback on the proposed changes. Plan to review the proposed changes and provide necessary feedback through the appropriate channels.
While it is not possible to comment on the extent of the changes of the regulations at this point, the first couple of sentences of the second paragraph of the executive order provide a hint that dramatic change is coming. “Incremental improvements will not give us the security we need; instead, the Federal Government needs to make bold changes and significant investments in order to defend the vital institutions that underpin the American way of life.” Keep this in mind as you move ahead with your security programs and monitor the progress of the regulatory changes as they make their way through public comment to final release.
ACT – Review your incident response plan
There are hints at some of the coming modifications to the regulations in the text, and Section 2(g)(i) states that recommendations for changes to the FAR Council on specific contract language will be provided by June 26, 2021. Some of the recommended changes will be around reporting of cybersecurity incidents. In one specific case, the timing of the reporting of cyber incidents will be based on a graduated scale of incident severity, with the most severe incidents requiring reporting within three (3) days of initial detection. Depending on the maturity of your incident response function, this timing could pose additional burden, in which case, you should review current procedures now with an eye toward satisfying the required timing for response.
WATCH – Guidelines for enabling software transparency
By July 12, 2021, standards, tools and best practices will be identified to enable the software transparency mission. By November 12, 2021, based on the initial investigation, preliminary guidelines for enhancing software supply chain security will be published. It’s not clear if those guidelines will be made public, but keep the date in mind and look for an opportunity to review, if available.
WATCH – Guidance publication
Based on the guidelines mentioned above, the Secretary of Commerce will issue guidance, including standards, procedures or criteria by February 12, 2022. This guidance shall include requirements to maintain accurate and up-to-date data of software and third-party components, to provide a Software Bill of Materials (SBOM) to purchasers directly or by publishing to a website, to employ automated tools that check for known and potential vulnerabilities which shall operate regularly or at a minimum prior to product, version or update release, to generate and provide artifacts that demonstrate conformance to the guidance, and others.
ACT – Develop Software Bill of Materials (SBOM) processes
Most organizations have little experience with the SBOM, so now is the time to do your due diligence and to begin putting processes, procedures, and policies in place for this inevitable requirement. If you have already begun generating SBOMs, you know the monumental manual effort involved. If you are unfamiliar with the SBOM, let’s start with the definition. The generally accepted definition of a product software bill of materials (SBOM) is a listing of the software components utilized in the product. Examples would include third-party operating systems or databases, along with proprietary algorithms. Sometimes it is expected that vulnerabilities associated with the specific components is included in the SBOM, but this varies by the party requesting the SBOM. There are various public resources that provide additional information on the SBOM, so we won’t attempt to replicate those in this document.
However, if you are interested in learning more about SBOM automation and vulnerability monitoring, we have an informative video showing how our SBOM platform makes generation simple and accurate. We also have other resources on our website that can help you navigate the complexity of the SBOM.
ACT – Vulnerability monitoring
Most organizations probably have some experience monitoring vulnerabilities, most likely through the use of the scanning tools that are available currently. However, even in these cases, it is likely that the associated processes and procedures are immature or informal. The most common implementation is a separation of SBOM and vulnerability monitoring, which results in a less-than-adequate security posture, given the proliferation of software component vulnerabilities and the required time commitment to research and determine applicability. The current common practice is to invest the manual effort to generate the product SBOM, and then to either put it on the digital shelf or start to work on discovering associated vulnerabilities. Given the many millions of currently reported vulnerabilities, with more being added daily, this is a never-ending task. Most organizations that get this far into the process, settle for a snapshot in time of product vulnerabilities. This is largely due to the functionality limitations of the scanning tools currently available, which require manual intervention and effort to research and determine applicability of current vulnerabilities to specific products. This semi-automated technique will not scale, and organizations will be quickly overrun. If you want to get out ahead of the coming tsunami and are interested in learning how to automate this process to combine SBOM generation and continuous vulnerability monitoring, you can check out our video, which we also mentioned in the prior section.
WATCH – Consumer labeling program
By February 12, 2022, internet of thing (IoT) cybersecurity criteria for a consumer labeling program will be identified. The focus will be on ease of use for consumers and will be modeled after existing labeling programs, such as the list of ingredients on food packaging. It is not hard to imagine the SBOM being leveraged for security labeling, which is additional motivation to start SBOM activity now. See the two prior sections labeled ACT.
WATCH – Establishment of a Cybersecurity Safety Review Board
The Board’s membership shall include Federal officials and representatives from private-sector entities. The purpose of the Board is to review and assess threat activity, vulnerabilities, mitigation activities, and agency responses. It’s not clear how the Board will carry out its mission, but there are mentions of protecting sensitive information provided to the Board and securing cooperation of affected individuals. It’s likely that the Board will monitor cybersecurity regulation and update, as needed.
WATCH – Adoption of National Institute of Standards and Technology (NIST) frameworks
The variability of current cybersecurity procedures across federal agencies is strong motivation for standardization and development of a set of operational procedures, referred to in the executive order as a playbook. The playbook shall incorporate all appropriate NIST standards. So, if you are not familiar with NIST cybersecurity documentation, such as the Cybersecurity Framework or the Secure Software Development Framework, now is the time to begin reviewing.
Conclusion
In summary, the executive order will bring massive changes to the way organizations plan, provide and communicate product security. The future looming deadlines for completion offer an opportunity to start preparing for these changes. By starting to develop processes and policies to address the new cybersecurity requirements now, organizations will save time, money, and possibly brand reputation, later. As we have suggested, there are specific actions that can be taken now, while in other cases, our recommendation is to monitor the progress of the development of the final requirement. In either case, by taking some proactive response, your organization won’t be caught by surprise.
In this document, we have provided suggestions for organizations on various aspects of the executive order, but for more information please see the complete document Executive Order on Improving the Nation’s Cybersecurity.






